Secure boot is a feature that is designed to ensure the integrity and security of a device’s boot process. It involves the use of digital signatures and public key infrastructure (PKI) to verify the authenticity of the boot process and prevent unauthorized software from being loaded.
It is typically used in devices that handle sensitive data or that are part of critical infrastructure, such as military systems, healthcare systems, telecom systems and financial systems.
So, in simple words we can say that secure boot ensures that only trusted, authentic and verified firmware will run on the embedded system.
Secure boot uses digital signature (≠ encryption) to verify the firmware. Kindly click here to read the difference between digital signing and encrypting.
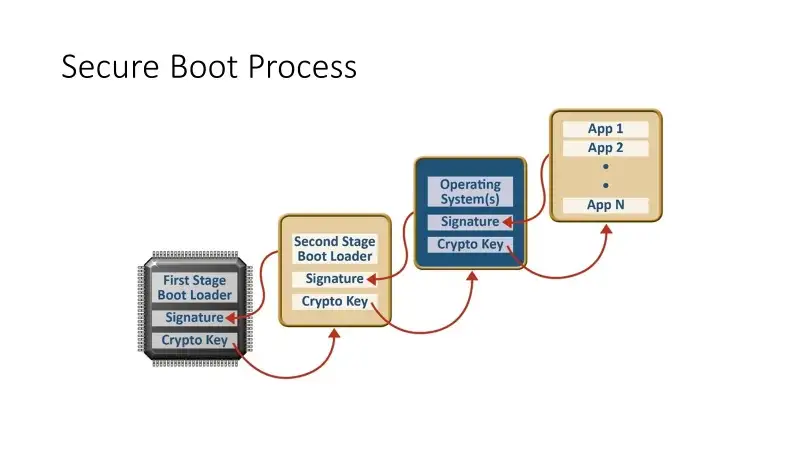
Secure boot works by using a chain of trust that starts with a trusted bootloader, which is a small program that is responsible for booting the system. The bootloader is signed with a digital signature, which is verified by a hardware-based secure boot mechanism to ensure that it is trusted and has not been tampered with. If the signature is valid, the bootloader is allowed to run and load the OS kernel and any other trusted software that is required to boot the system. So, we can say that the Secure boot typically operates as follows:
- A device’s firmware, such as the BIOS or UEFI, is configured with a list of trusted public keys.
- When the device is powered on, the firmware verifies the authenticity of the bootloader using the trusted public keys. If the bootloader is not authenticated, the device will not boot.
- The bootloader verifies the authenticity of the operating system kernel using the trusted public keys. If the kernel is not authenticated, the device will not boot.
- The operating system kernel verifies the authenticity of any additional software or drivers that are loaded during the boot process using the trusted public keys. If any of these components are not authenticated, they will not be loaded.
In addition to verifying the authenticity of the bootloader, secure boot also protects against malware and other types of attacks by preventing unauthorized software from being loaded and run on the system. This can help to protect against malicious software that may try to install itself on the system or modify system files in an attempt to gain access to sensitive data or disrupt system operation.
What are Secure boot public keys:
Public keys are an essential part of secure boot, which is a feature of modern computer systems that ensures that only software that is signed with a trusted key can be loaded and run at boot time. Public keys are used to verify the authenticity of signed software and ensure that it has not been tampered with. The public keys are stored in the firmware of the computer and are used to verify the signature of the bootloader and other critical software components.
There are typically two types of public keys used in secure boot: platform keys and key exchange keys.
Platform keys are used to verify the authenticity of the bootloader and other critical system software, such as the operating system kernel. These keys are usually provided by the manufacturer of the computer and are stored in a secure location in the firmware. The system will only boot software that is signed with one of these trusted platform keys.
Key exchange keys, on the other hand, are used to establish trust between different components of the system, such as between the bootloader and the operating system. These keys are used to create a chain of trust, allowing the system to verify the authenticity of each component as it is loaded.
Where is the Secure Boot Public keys stored:
As mentioned above, a device’s firmware such as BIOS/UEFI/TPM etc. are configured with public keys. Now let us try to understand how these keys are stored into these.
- Firmware-based secure boot mechanisms are typically used in devices that do not have a TPM or that do not support UEFI. These mechanisms are similar to UEFI and TPM systems in that they use a public key infrastructure (PKI) to manage the secure boot keys and certificates, and the keys are stored in a secure location within the firmware.
- BIOS-based secure boot mechanisms are typically used in older devices that do not support UEFI or TPM. These mechanisms are similar to firmware-based secure boot mechanisms in that they use a PKI to manage the secure boot keys and certificates, and the keys are stored in a secure location within the BIOS.
- In UEFI systems, secure boot keys are typically stored in the UEFI firmware itself. The keys are used to verify the authenticity of the bootloader and any other trusted software that is required to boot the system. UEFI systems use a public key infrastructure (PKI) to manage the secure boot keys and certificates, and the keys are stored in a secure location within the UEFI firmware.
- In TPM systems, secure boot keys are stored in a hardware-based secure boot mechanism called a Trusted Platform Module (TPM). The TPM is a hardware component that is designed to store and manage secure keys and other sensitive data in a secure manner. TPM systems use a PKI to manage the secure boot keys and certificates, and the keys are stored in a secure location within the TPM.
Process of signing and verification of secure boot:
The process of signing and verification of secure boot involves the following steps:
- The developer of the software creates a private key and a corresponding public key. The private key is kept secret and is used to sign the software. The public key is shared publicly and is used to verify the authenticity of the signed software.
- The developer signs the software using the private key. This creates a digital signature that is attached to the software.
- The signed software is then distributed to the users.
- When the user attempts to boot the software, the system checks the signature using the public key. If the signature is valid, the system will boot the software. If the signature is invalid or the public key is not trusted, the system will not boot the software and will instead display an error message.
- If the signature is valid and the system boots the software, the system may also verify the authenticity of other components, such as the bootloader and the operating system kernel, using the same process. This creates a chain of trust, ensuring that only trusted software is allowed to run on the system.
By using this process, secure boot helps to protect against malicious software, such as viruses and rootkits, that might try to infect the system or compromise its security. However, it is important to keep the system up to date with the latest security patches and to use other security measures, such as antivirus software and firewalls, to help protect against malware.
